Okta Authentication
Cloudify enables integration with your local Okta system to authenticate users and provide Role-Based Access Control. This guide describes the configuration steps required to enable Okta authentication.
Other SAML 2.0 authentication solutions can be integrated with Cloudify. However, only Okta is tested and officially supported.
To enable Okta integration, the openssl package on Cloudify Manager needs to be of version 1.0.2. If you are running a Cloudify image this is already the case, however if you are installing Cloudify make sure to update the openssl package prior to the Okta configuration.
Part 1: Configuring Okta
To configure Okta authentication in Cloudify, first add Cloudify as an application in your Okta system.
Okta Configuration Prerequisites
You’ll need Okta administrator privileges and your Cloudify IP address/URL (or load balancer IP address/URL for Cloudify HA cluster configuration).
Adding Cloudify as an Okta Application
- Open the Okta Admin dashboard
- From the top menu, choose Applications > Applications > Create App Integration
- In the Create a new app integration form, choose SAML 2.0 as sign-in method
- In the General Settings step, configure the application name, such as Cloudify Dev and add the logo.
In the Configure SAML step, configure the following in the SAML Settings section:
In General subsection:
- add the Single sign on URL: https://cloudify-manager-ip/console/auth/saml/callback
- make sure the box for Use this for Recipient URL and Destination URL is checked.
- add the Audience URI: https://cloudify-manager-ip/console/auth/saml/callback
In Attribute Statements subsection add the following:
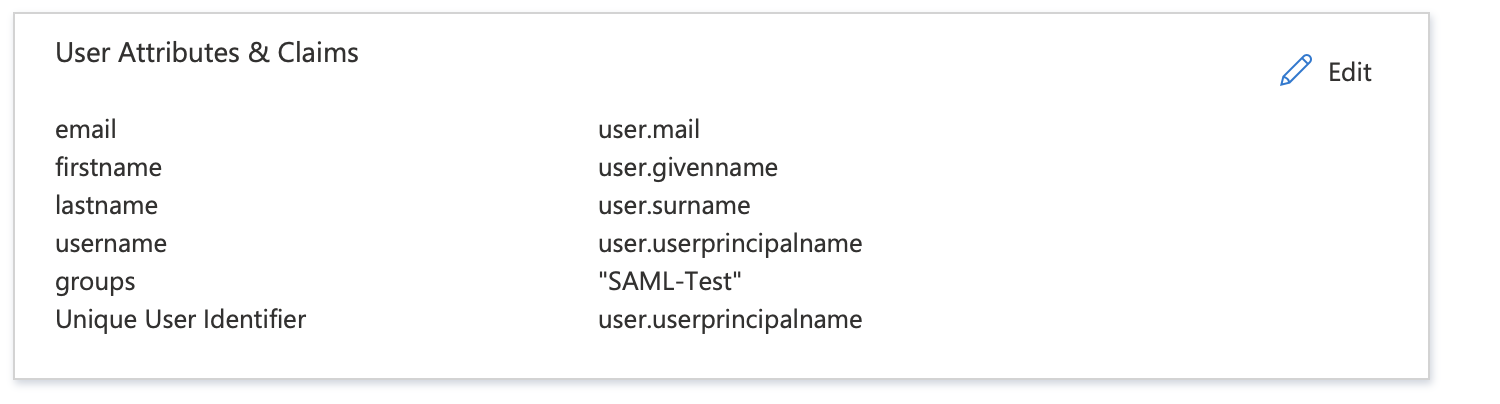
- Name - firstname, Name Format - unspecified, Value - user.firstName
- Name - lastname, Name Format - unspecified, Value - user.lastName
- Name - email, Name Format - unspecified, Value - user.email
- Name - username, Name Format - unspecified, Value - user.login
In Groups Attribute Statements subsection add all relevant user groups, or generally use:
- Name - groups, Name Format - unspecified, Filter - Regex, Value - .*
In the Feedback step, define Cloudify as an internal app
Once a new Cloudify integration is created, you need to create at least one group in Directory > Groups section and assign relevant users to it.
Additional Configuration
- Provide the Okta Identity Provider Single Sign-On URL and X.509 Certificate to the Cloudify Manager administrator. They can be found in: Application page > Sign on tab > Settings section > Sign on methods > View Setup Instructions
Part 2: Configuring Cloudify
To complete the Okta authentication configuration, Okta needs to be configured in the Cloudify Manager.
Cloudify Prerequisites
You’ll need the following:
- SSH access to the Cloudify VM/s with
sudoprivileges - Okta CA Certificate (provided by your Okta administrator)
- Identity Provider Single Sign-On URL (provided by your Okta Administrator)
Adding Okta Authentication in Cloudify
SSH into the Cloudify Manager VM and follow these steps:
- Add the Okta certificate for Cloudify (provided by your Okta admin, see above). Save the certificate as
okta_certificate.pemin/etc/cloudify/ssl/ Restart Cloudify REST service using the following command:
sudo supervisorctl restart cloudify-restserviceConfigure the Cloudify Management Console to use Okta with the following steps:
Copy default user configuration file to user data folder
sudo -u stage_user cp /opt/cloudify-stage/conf/userConfig.json /opt/cloudify-stage/dist/userDataOpen the file
/opt/cloudify-stage/dist/userData/config.jsonfor editingUnder
samlsection change the values as follows:enabled: true (enabling SAML mode)certPath: “/etc/cloudify/ssl/okta_certificate.pem” (SAML certificate path which is used by the Cloudify Manager and Cloudify Management Console)ssoUrl: <okta_sso_url> (redirect url to the application, Identity Provider Single Sign-On URL which can be found under Setup Instructions section of the newly created Cloudify app in Okta)portalUrl: <organization_okta_portal_url> (redirect url to the organization portal: https://my-org.okta.com)
Remove all other configuration objects (except
saml) from the file if you don’t plan to modify it
Restart the Cloudify Management Console service using the following command:
sudo supervisorctl restart cloudify-stage
Create new user-groups in Cloudify, matching the user groups in Okta (must be exactly the same names) using the following command for each group:
cfy user-group create <user_group_name> -r <security-role>Assign the user-groups to tenants using the following command:
cfy tenants add-user-group <user_group_name> -r <role> -t <tenant_name>
Adding Okta Authentication in Cloudify HA Configuration
- The Load Balancer IP address (or URL) should be used for SSO URL in Okta
- Each Cloudify manager in the HA cluster must be configured according to the steps above.
Configuring Azure SSO
To configure Azure-SSO authentication in Cloudify, first you need to create an enterprise application for Cloudify on your Azure Account.
Azure-SSO Application Setup
After you create an enterprise application you need to configure Single sign-on with the following sections:
Basic SAML Configuration:
- Identifier (Entity ID) : https://cloudify-manager-ip/console
- Reply URL (Assertion Consumer Service URL) : https://cloudify-manager-ip/console/auth/saml/callback
Attributes & Claims: [ Same as in Part-1 Above ]
Note make sure to not include any namespace
- SAML Certificates:
- from edit -> SAML Signing Certificate
- change the Signing Option to : Sign SAML response
Note Make sure to download the certificate [Certificate (Base64)]
To get the user access URL , from application properties: User access URL
Then you need to follow Configuring Cloudify above - with these values override:
- ssoUrl : the user access URL that you got above
Configuring WSO2 SSO
To configure WSO2-SSO authentication in Cloudify, first you need to create a service provider for Cloudify on your WSO2 Setup.
WSO2-SSO Service Provider Setup
After you create a service provider you need to configure Single sign-on with the following sections:
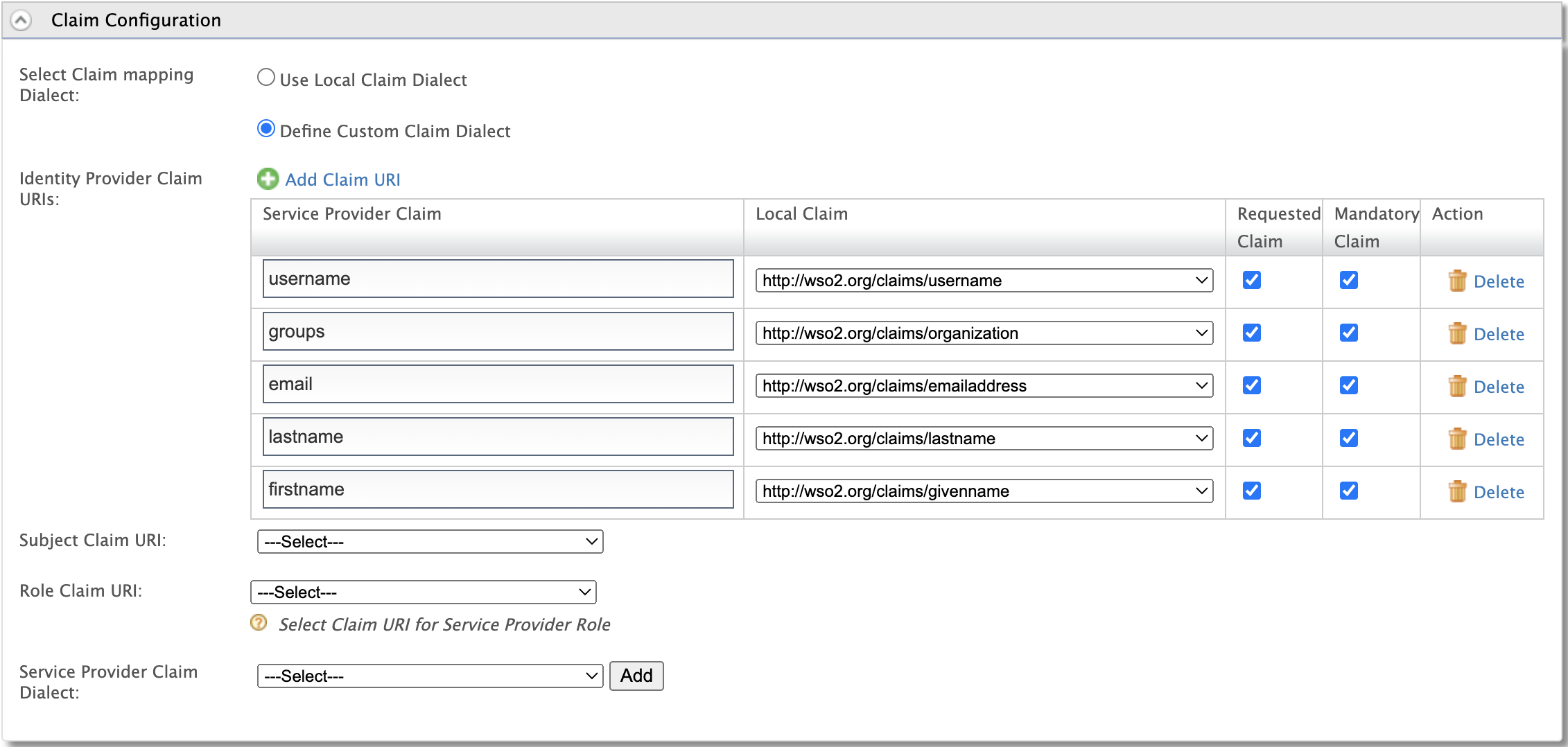
- Claim Configration: [ Same as in Part-1 Above ]
Note make sure to not include any namespace
- Define Custom Claim Dialect
- Inbound Authentication Configuration:
- SAML2 Web SSO Configuration:
- Issuer: console
- Assertion Consumer URLs : https://cloudify-manager-ip/console/auth/saml/callback
- Enable Response Signing : [ Tick it ]
- Enable Signle Logout: [ Tick it ]
- SLO Request URL : https://cloudify-manager-ip/console/login
- Logout Method : Front-Channel Logout (HTTP Redirect Binding)
- Enable Attribute Profile : [ Tick it ]
- Include Attributes in the Response Always : [ Tick it ]
- Enable IdP Initiated SSO
- Enable IdP Initiated SLO
- Return to URL : https://cloudify-manager-ip/console/login
- Download IDP Metadata
Note the certificate will be part of IDP Metadata file so you need to get it from the XML
Then you need to follow Configuring Cloudify above - with these values override:
