GCP GKE
This example demonstrates provisioning a Google Kubernetes Engine (GKE) cluster on the GCP cloud. The deployment consists of:
- GCP GKE cluster
- Security group
- Network
- All of the essential peripherals in GCP (IP address, NIC, etc.)
In this example, we will deploy only the cluster. Later, in the more advanced examples (multi-cloud examples) we will leverage this setup as the basis for deploying a containerized service.
Prerequisites
This example expects the following prerequisites:
- A Cloudify Manager installed and accessible
- This can be either a Cloudify Hosted service trial account, a Cloudify Premium Manager, or a Cloudify Community Manager
- Access to GCP infrastructure is required to demonstrate this example
Cloudify CLI or Cloudify Management Console?
Cloudify allows for multiple user interfaces. Some users find the Cloudify Management Console (web based UI) more intuitive while others prefer the Cloudify CLI (Command Line Interface). This tutorial and all following ones will describe both methods.
Community version - Some of the options described in the guide are not available in the community version management console (web UI). An example would be setting up secrets. You can still perform all of the functionality using the Cloudify CLI.
Cloudify Management Console
This section explains how to run the above described steps using the Cloudify Management Console. The Cloudify Management Console and Cloudify CLI can be used interchangeably for all Cloudify activities.
Import Plugins and Secrets
To connect to GCP, credentials and Cloudify plugins are required. Cloudify recommends storing such sensitive information in a Cloudify secret. Secrets are kept encrypted in a secure way and used in run-time by the system. Learn more about Cloudify secrets here.
GCP credentials can be created by following the guide here.
To store the access keys as secrets in the Cloudify Manager, log in to the Cloudify Management Console and select the Resources page. In the Secrets panel, scroll to the Secret Store Management widget and use the Create button to add the following new secret:
- gcp_credentials
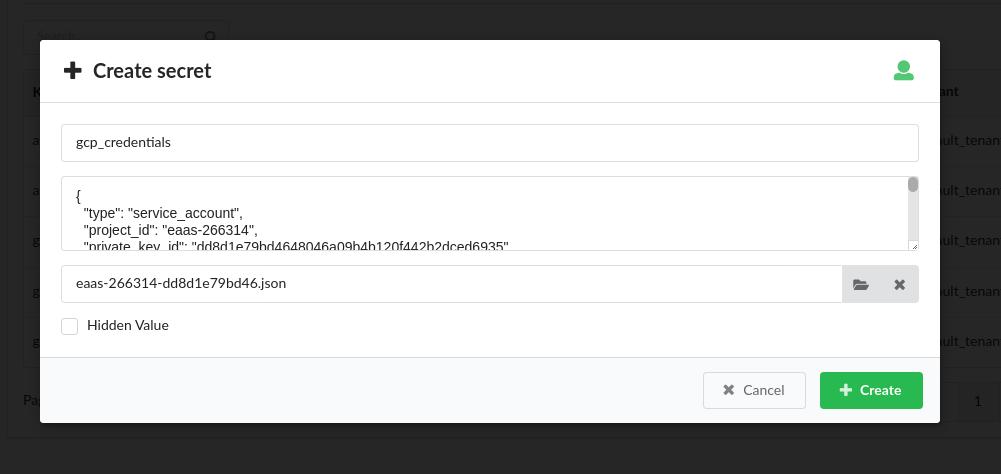
Validate Secrets
To view the imported secrets in the Cloudify Manager, log in to the Cloudify Management Console and select the Resources page and navigate to the Secrets tab. The following secrets should exist after following the above steps:
- gcp_credentials
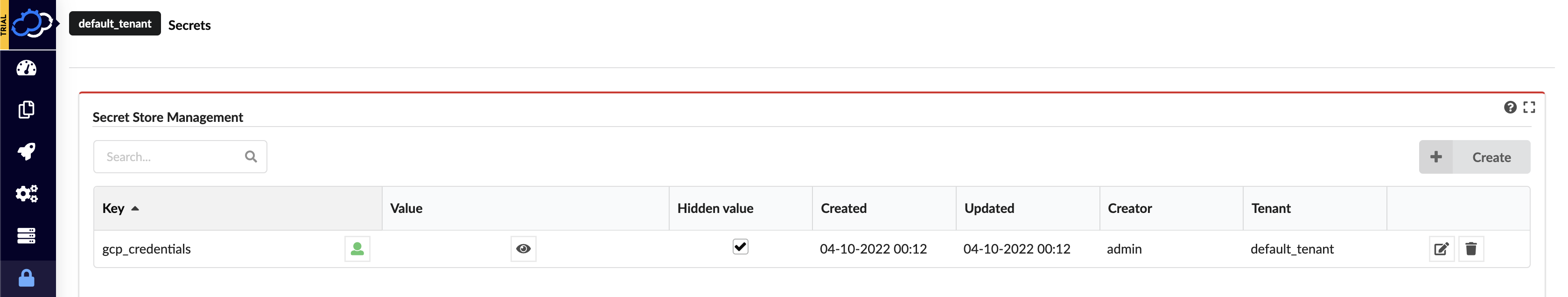
Import Kubernetes Blueprint
The Cloudify Manager provides an easy method of provisioning a Kubernetes cluster on GCP GKE. On the Marketplace page, navigate to the Kubernetes Blueprint Examples tab and upload the Kubernetes-GCP-GKE blueprint. Once the blueprint will be uploaded you’ll be redirected to create a deployment dialog.
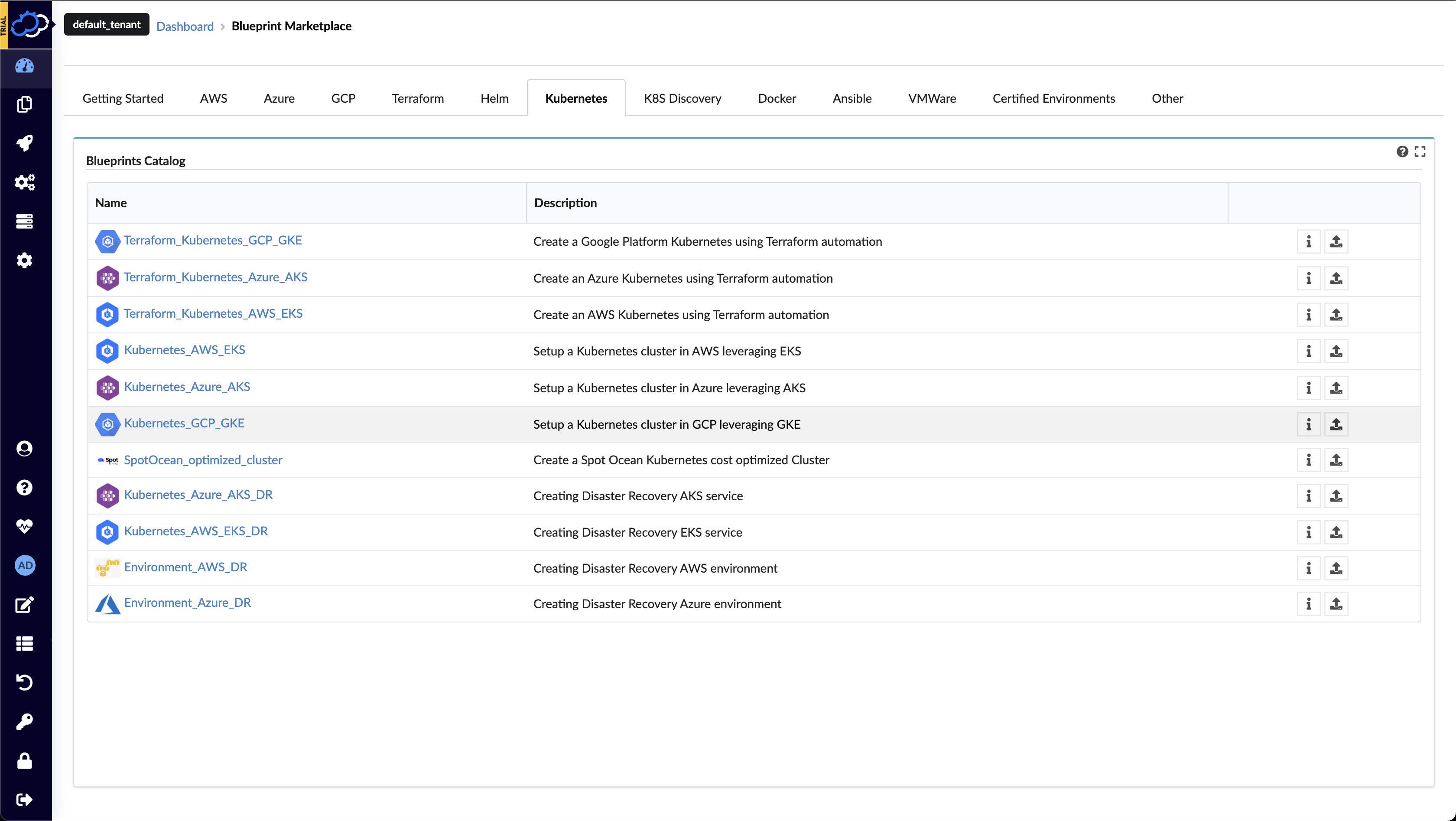
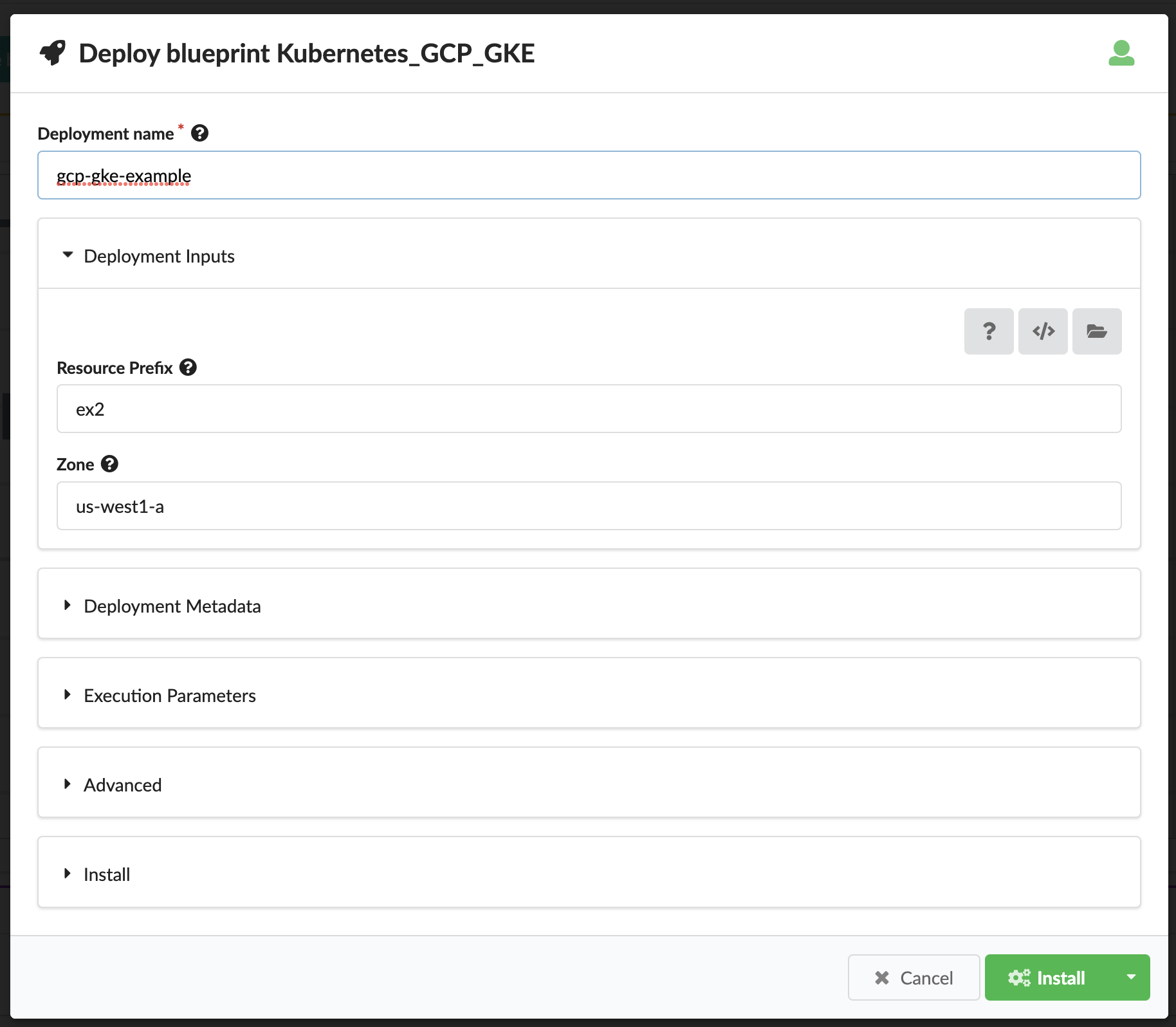
Deploy a GCP GKE Cluster
- Create a Deployment name
- Adjust the Zone input to match your preferences
Click the Install button at the bottom of the form to start the deployment. On the following page, click the Execute button.
You now have a Cloudify Deployment running the default install workflow. Cloudify will begin actively interfacing with GCP to deploy a GCP GKE Kubernetes cluster. You can track the status of the Deployment in the Execution Task Graph panel on the Deployments page.
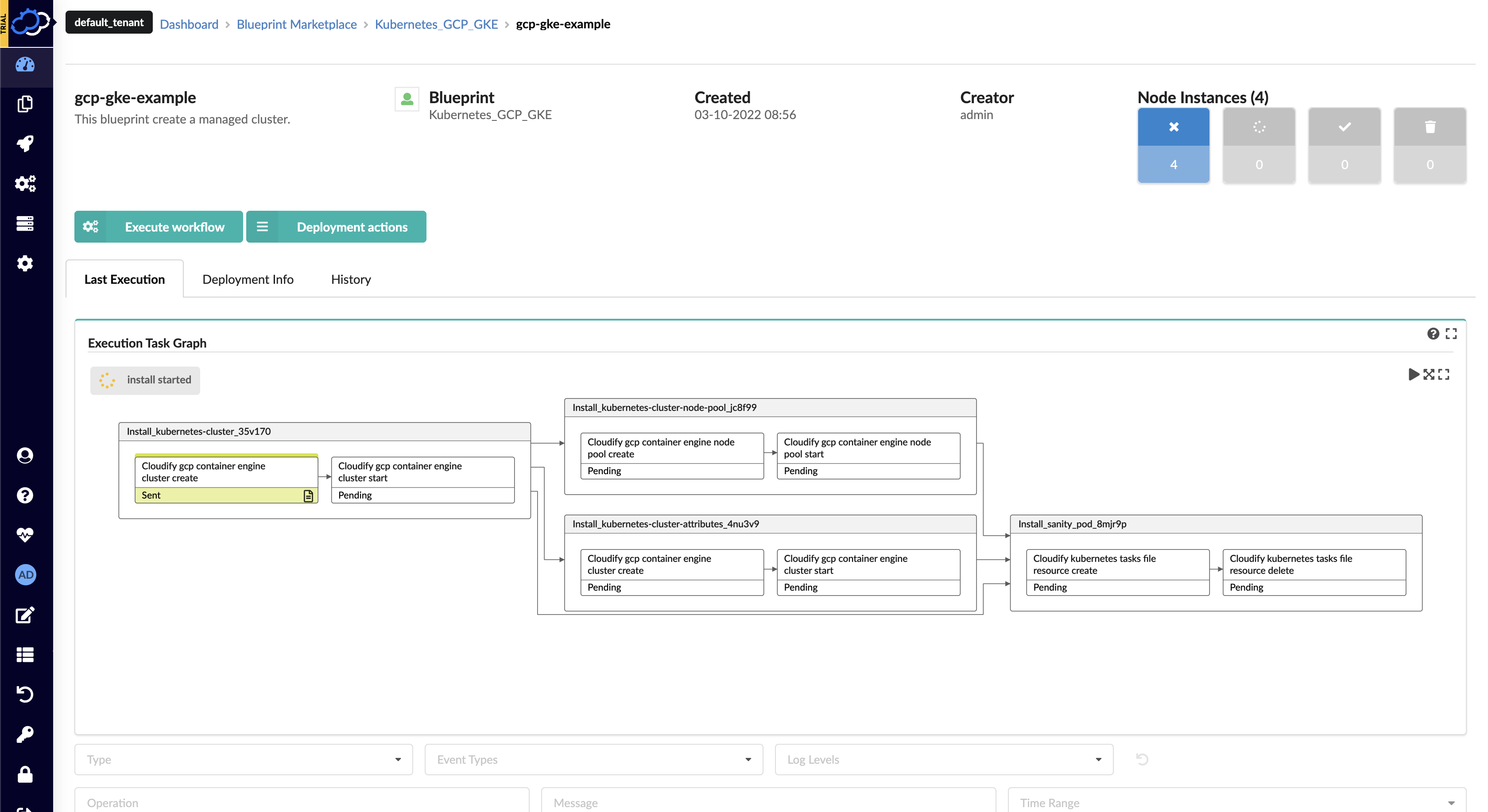
Using the GCP GKE Cluster
Install CLI Tools
Kubectl
GCP documentation: https://docs.aws.amazon.com/eks/latest/userguide/install-kubectl.html
GCP CLI
GCP documentation: https://cloud.google.com/sdk/docs/install
To initialize Kubectl, go to the GCP Console, navigate to the Kubernetes Engine page and in the dropdown for your cluster, click Connect. This will display a CLI command to use to set up the Kubectl config.
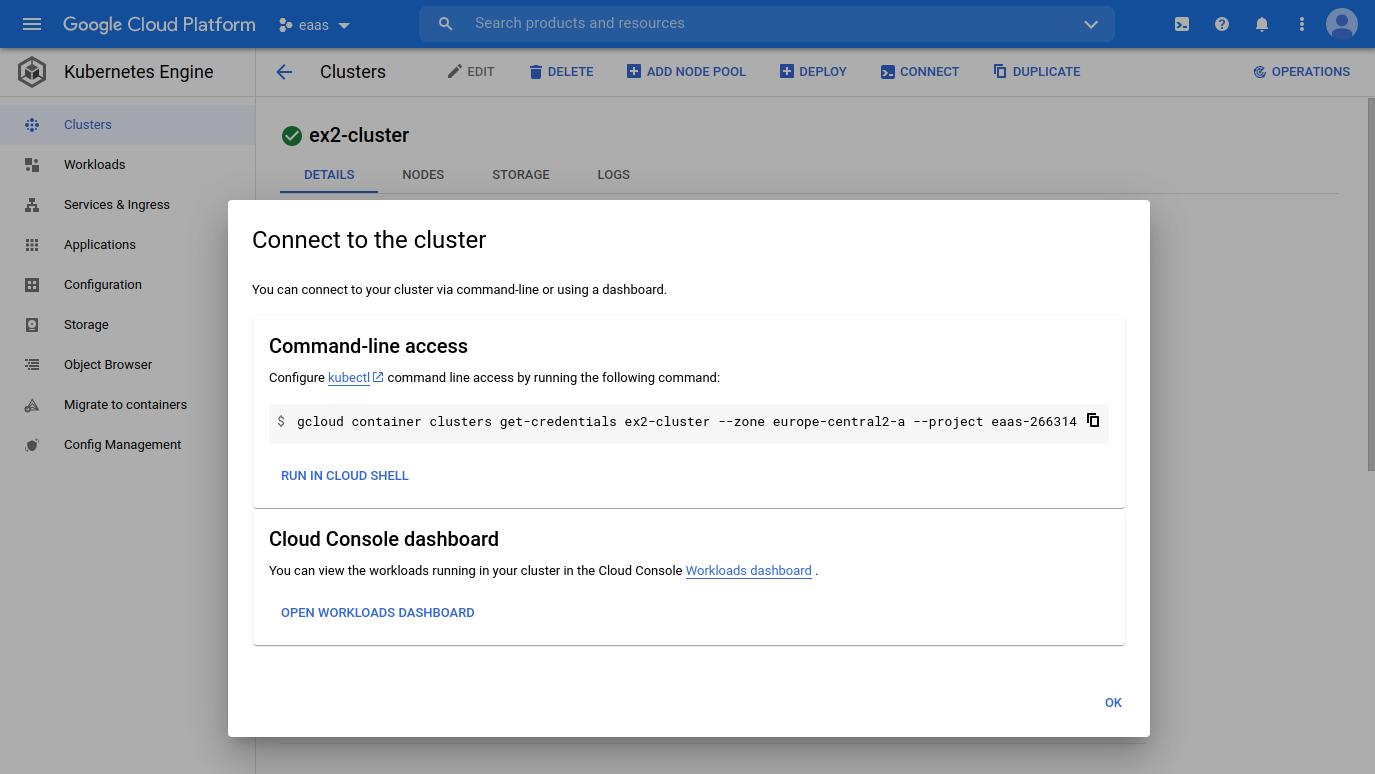
# Example GKE Kubectl init command
gcloud container clusters get-credentials ex2-cluster --zone europe-central2-a --project eaas-266314Verify Access
# List version
kubectl version --kubeconfig ~/.kube/config
# List namespaces
kubectl get ns --kubeconfig ~/.kube/config
# List nodes
kubectl get nodes --kubeconfig ~/.kube/config